The Jolocom Protocol - Own Your Digital Self¶
The Jolocom identity solution aims to be a universal, lightweight, open source protocol for decentralized digital identity and access right management.
The Jolocom stack aggregates a number of existing specifications, largely adopted within the SSI community, and aims to simplify the creation / management of digital identities (including the associated data such as Verifiable Credentials), as well as enable for more complex interactions between the aforementioned identities.
The core specifications on which the Jolocom protocols build are:
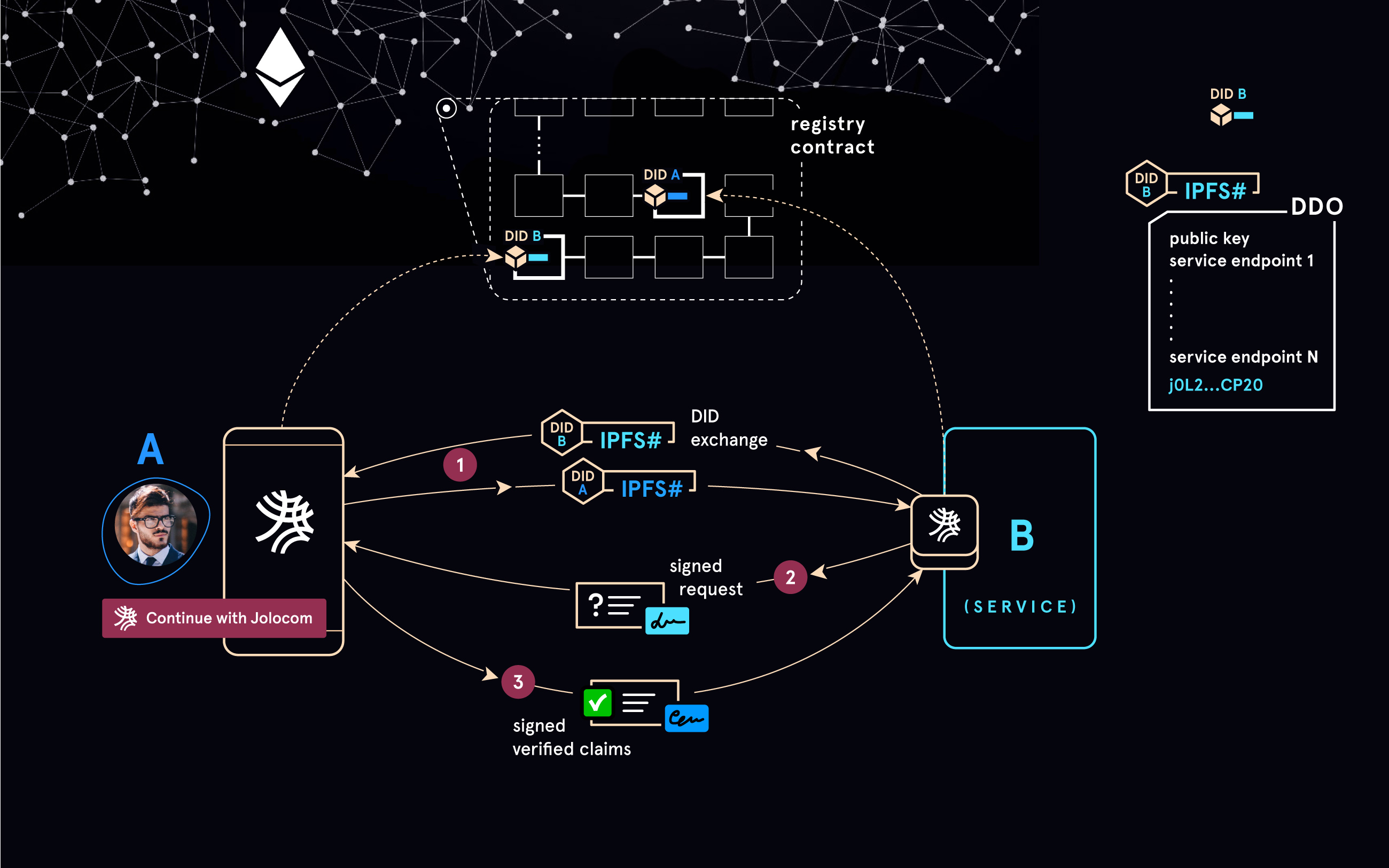
- Decentralized Identifiers (DIDs) - every entity making use of the Jolocom stack needs a DID if it wishes to issue / receive Verifiable Credentials, or initiate / participate in interactions with other Jolocom identities. The DID specification allows each agent in the network to generate a decentralized identifier and register / anchor it (the implementation of this operation is normally defined in the corresponding DID Method specification). Once an identity has been “anchored”, the corresponding DID will become resolvable by other network participants, and can be used as part of various supported interactions (e.g. for issuing and receiving Verifiable Credentials).
- Verifiable Credentials - this specification allows us to model / express statements made by one identity / DID (in this context - issuer) about another one (in this context - subject). Any identity can ensure that a Verifiable Credential they are presented with has been issued by the listed issuer, and has not been tampered with / modified (e.g. by a malicious holder, or other parties involved in the interaction) due to the inclusion of digital signatures (generated by the signing keys associated with the issuer’s DID).
The Jolocom protocol can be used to:
- Create self-sovereign identities (e.g. for humans, organizations, smart agents).
- Associate information with the aforementioned identities in the form of Verifiable Credentials.
- Undertake interactions between identities in order to easily share / receive verifiable information.